Ransomware is real
It’s not a matter of if anymore, only a matter of when. Recovery from a ransomware attack is not easy. How do we recover a machine if we can’t trust any files on the local machine, we can’t trust the operating system, and we can’t even trust our own internal IT servers to deploy a new OS cleanly?
Overview
2Pint Software offers several technologies that make recovery from real world ransomware attacks easier. Our state-of-the art technologies include:
- iPXE Anywhere - Can boot to a recovery operating system without touching the local disk which may be quarantined.
- Peer-to-peer – Our suite of peer-to-peer technologies can install new operating systems and applications with minimal impact on your network.
- And more! – Depending on circumstances, 2Pint Software recovery solutions may include PowerShell Deployment (PSD), DeployR, Autopilot, and other technology.
With 2Pint Software, during a real-world ransomware attack, your employees and your business can get back to work with less disruption.


Ransomware recovery
When a ransomware attack happens, time is not your friend. Your organization loses revenue and productivity every hour, every day, and every week your systems are down. Affected endpoints may include:
- Business critical banking, manufacturing and point of sale systems
- Employee desktops and laptops
- Server systems
Getting your systems up and running again is a top priority.
But the path to recovery can be a chicken-and-egg scenario. How do we get our systems up and running again if the systems typically used to recover IT assets may be compromised?
Typical case
A typical ransomware scenario could develop as follows:
- Employee Bob opens an e-mail attachment that contains malware.
- Bob is a local administrator on the box, so his user credentials provide full access to the box.
- Using techniques found in the Mimikatz exploit, the attackers traverse the corporate network to install their malware packages.
- When enough machines are infected with malware, attackers encrypt and lock critical files – or even the entire operating system.
- A ransom is demanded to provide the keys to unlock the files. Will the negotiations be successful?
There are several great solutions on the market to help mitigate some of the vulnerabilities listed above (shame on Bob for opening the attachment 😊).
But IT departments need to be prepared for the worst-case scenario: that no recovery is possible, and all machines must be wiped and re-installed.
The challenge
During a real-world ransomware scenario, we may need to start recovering machines from various locations. That includes each branch office location, and wherever remote workers are based.
With internal systems compromised, the cloud anchors our strategy for rebuilding the recovery environment.
Enter RecoveR
RecoveR from 2Pint Software gives customers the ability to install a new OS from the cloud. We first boot into iPXE, and then into WinPE (Windows Pre-installation Environment) from the cloud – without the need for local infrastructure.
We can then install a new OS using any system already in place, or a public system like PSD (PowerShell Deployment). All content is downloaded using BranchCache for speed and efficiency.
Technology
- iPXE (iPXE.org) - A public standard for booting to a recovery environment over the network.
- BranchCache – Microsoft technology for peer-to-peer downloading.
- PSD (PowerShell Deployment) – Powerful scripting tools for OS deployment.
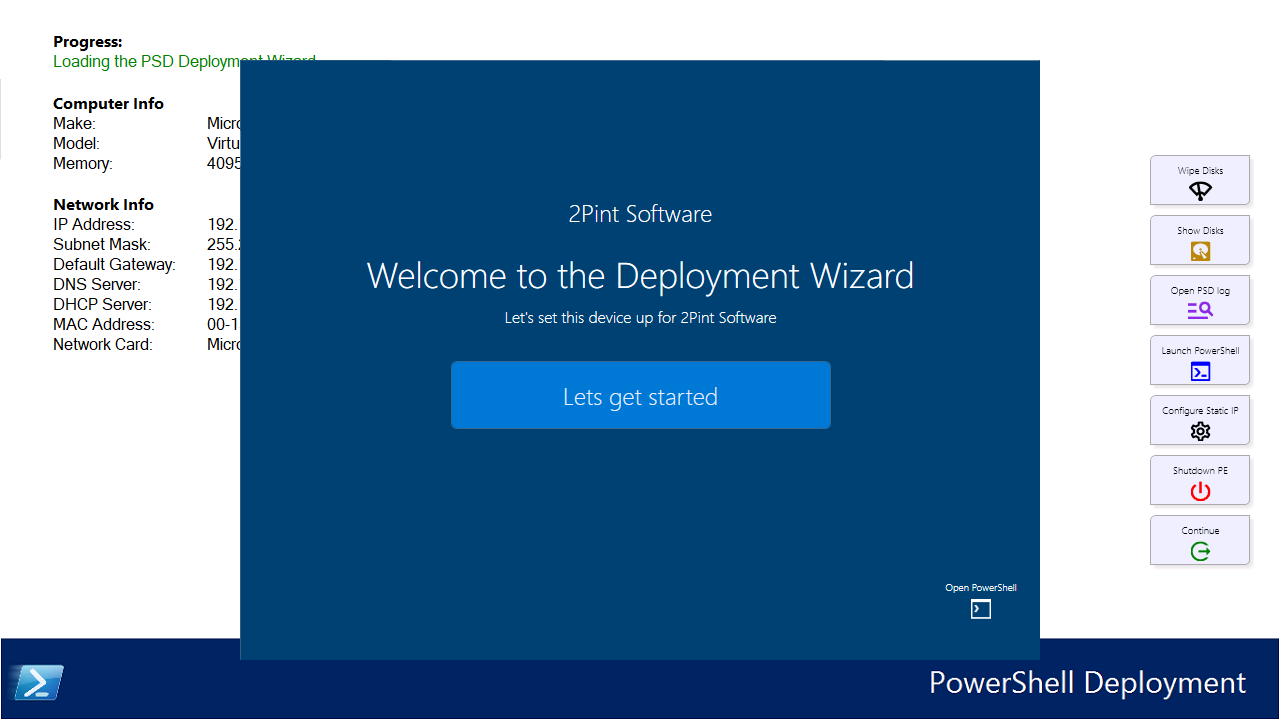
In more detail
Once a ransomware attack has occurred, you will need to make some assessments quickly to determine where to go next.
- Are on-premise directory services compromised? Or should we move to Entra ID?
- Are on-premise Exchange or SharePoint servers compromised? Or should we move to Microsoft Cloud PKI?
- Are deployment and/or application servers available? Or should we move to the cloud?
- What kind of ransomware tech was used to compromise your machines? Was it just a script to BitLocker encrypt your machines with a new security key? Or something more advanced, like attacks in firmware? If more advanced, we may need to order new machines, delivered directly to employees and offices and deployed with Autopilot. 2Pint Software can help.
If we determine that it’s necessary to rebuild existing machines, we can use iPXE to remote boot machines to WinPE. Either:
- We can pre-load all machines with a UEFI HTTPS boot URL, and HTTPS boot certificate.
- For local machines, we can simply stand up an iPXE server. With the correct changes to DHCP, there is no need to setup PXE servers on every subnet.
- Or finally, we can provide USB boot sticks (about 5mb) to reboot machines to iPXE.
Once booted to iPXE, we can download our WinPE image, either over the internet, or cached on a peer in our offices. From WinPE, we can download and install a full OS – again over the internet, or cached on peers in our office. Apps can easily be installed using peer-to-peer technology as well.
The installation of the new OS can be entirely done without unencrypting the local infected disk. We can also script our recovery solution to backup/archive the local infected disk to cloud storage if we need to recover later.
2Pint Software technology used:
- iPXE Anywhere - with 2Pint Software, we supply Secure Boot signed binaries, and support downloading of the WinPE WIM file using BranchCache peer-to-peer technology. We have many customizable menus to be able to cater to any deployment scenario.
- StifleR – We peer-to-peer your OS builds and track all the OS deployment and Autopilot build analytics.
Works with the following Microsoft technology:
- BranchCache – Get control of your peer-to-peer downloads using StifleR and other technologies from 2Pint Software to speed up your network.
- PSD – We provide direct integration with PSD (PowerShell Deployment).
- Windows Autopilot
- WinPE
Learn more
Like to know more about ranswomware recovery from cloud? We can help you to get things going in your own environment.