Ransomware is a growing threat to organizations
In 2023 ransomware attackers extorted more than 1.1 billion dollars from organizations around the world. The total cost in lost productivity and remediation was much higher. By reducing the number of end users with administrative privileges it is estimated that 92% of malware and ransomware attacks can be prevented.
Overview
Microsoft recently released Microsoft Intune Endpoint Privilege Management which can elevate permissions when necessary.
However, removing administrative privileges is extremely challenging in an enterprise due to the lack of visibility into where and how administrative privileges are being used.


Threat vector identification
Administrators often struggle to identify important information:
- How many endpoints have users logging on with administrative permissions?
- How many endpoints are running elevated processes?
- Are domain administrators logging on to endpoints?
- Is User Access Control configured properly across the enterprise?
Typical case
In an ideal world, IT departments would deploy all their endpoints at the same time, with common operating system versions. Devices would be fully patched and run the same software and drivers. Computers would operate in identically configured network environments with continuous Internet connectivity and IT managers would easily track updates and admin permissions.
The reality is much messier. Personnel come and go, and they work in multiple locations and time zones. Users need different role-specific software installed and permissions opened. Depending on the nature of their work they can have uneven and unpredictable requirements. Even the most diligent IT support staff may overlook a potential threat vector when managing hundreds or thousands of variably configured endpoints.
The challenge
What IT departments need is a readily accessible and efficient method to quickly check all enterprise endpoints for elevated permissions. Equipped with critical and timely information, managers can review privilege settings, identify active administrative processes, and remediate potential security threats.
Enter StifleR + InTune
With 2Pint Software's StifleR organizations gain real-time visibility into User Access Control settings and strategic security intelligence on user privileges across the enterprise.
Real-time visibility
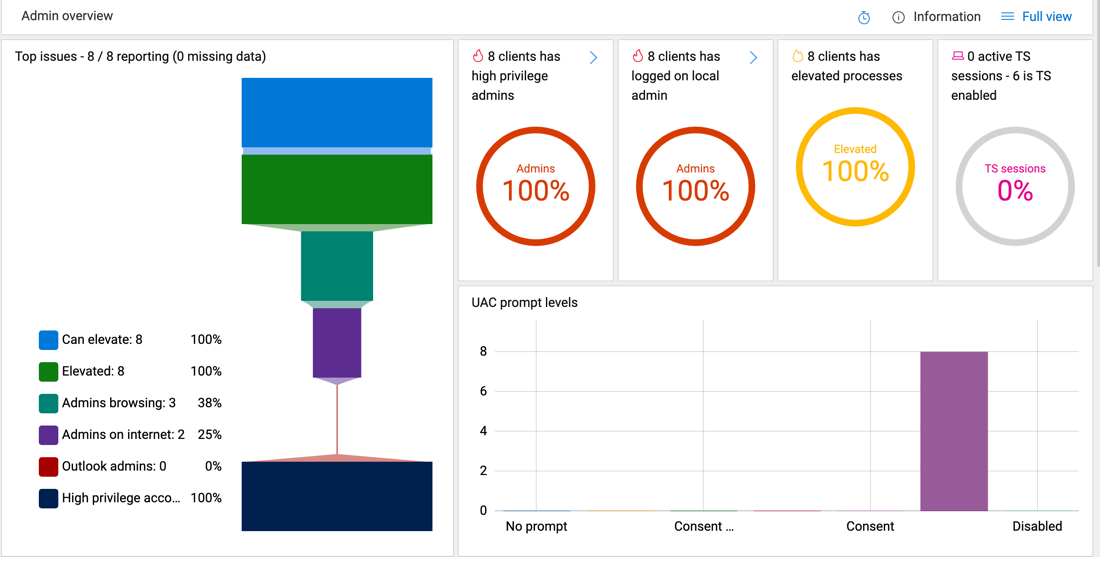
The StifleR dashboard view displays the following information:
- Number of users logged on with administrative permissions
- Number of users with highly privileged domain accounts
- Number of users that can elevate permissions
- Number of users that have elevated processes
- Number of administrators that are actively browsing the Internet
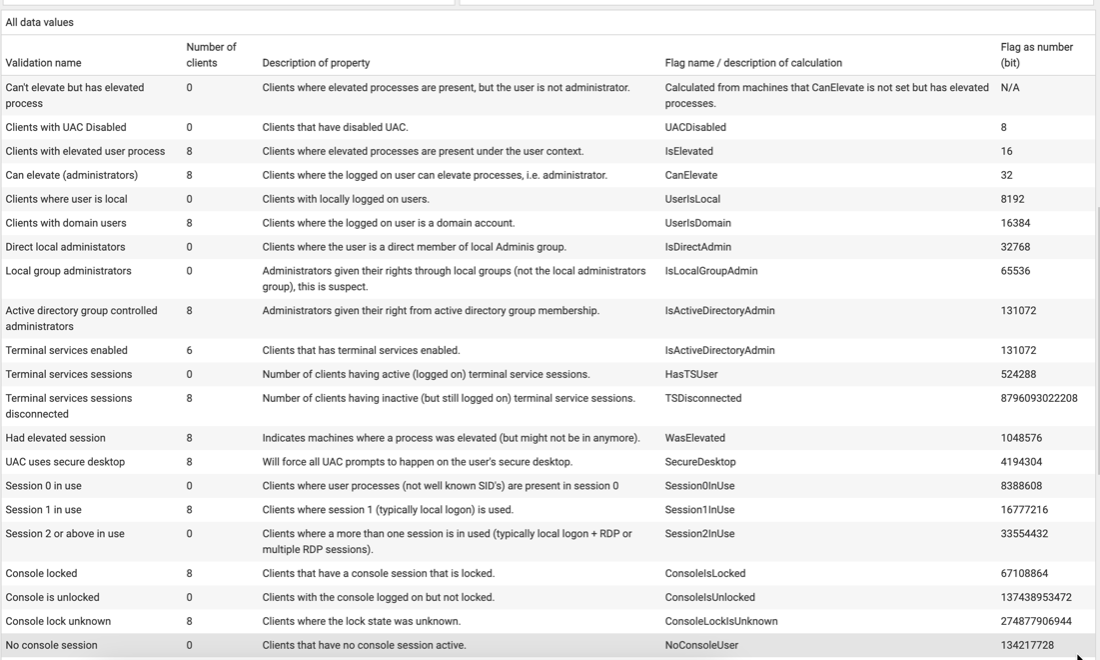
Comprehensive privilege data
StifleR also exposes many other settings related to privileges with a sampling shown in this table.
In more detail
After endpoints currently running with administrative privileges have been identified it is possible to strategically tighten security. Administrative rights can be eliminated where feasible and elevation policies can be pushed out with Microsoft Intune Privilege Management to only permit when needed.
By combining the capabilities of 2Pint Software’s StifleR and Microsoft Intune Endpoint Privilege Management access to administrative rights can be greatly limited and exposure to malware and ransomware reduced by 92%!
For more information about this technology see the following:
2Pint Software technology used:
- StifleR Enterprise for bandwidth management and automation
Works with the following Microsoft technology:
- Microsoft Intune (requires the StifleR agent)
Learn more
Like to know more about securing your network with StifleR and Microsoft Intune Endpoint Privilege Management? We can help you to get things going in your own environment.